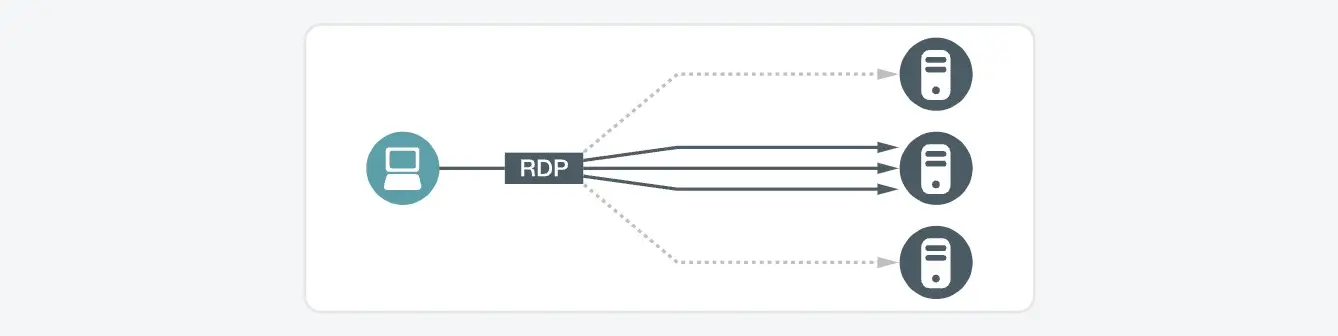
Triggers
- A host is making multiple RDP connection attempts with most of the connections failing to complete
- The connection attempts can target one or more RDP servers
- Even when a single RDP server is targeted, multiple accounts may still be involved in the encrypted part of the RDP connection setup
Possible Root Causes
- An attacker is trying to determine the existence of accounts in order to progress to the next step in the attack
- The attacker is working through a list of accounts with well-known default passwords in an attempt to find a working account/password combination
- This host is a jump server and several users are unsuccessfully attempting to RDP to other servers from it
Business Impact
- A scan via RDP is an effective way for an attacker to determine what accounts are available inside an organization’s network and which RDP servers accept logins via the accounts
- If one of the targets has not been normally accessed via RDP, the nature of the target server will provide additional guidance regarding the potential business impact
- Reconnaissance within a network is a precursor to active attacks which ultimately exposes an organization to substantial risk of data acquisition and exfiltration
- This form of reconnaissance is often a lot less noticeable than a port sweep or a port scan so attackers feel they can use it with relatively little risk of detection
Steps to Verify
- Inquire whether the target of the RDP connection attempts should even be setup to accept RDP connections
- Inquire whether this host should be initiating the number of RDP connections to the targets listed in the detection
- If this host is a jump server, retrieve the logs of the jump server to see what upstream connections are the originators of the large number of failed RDP connections