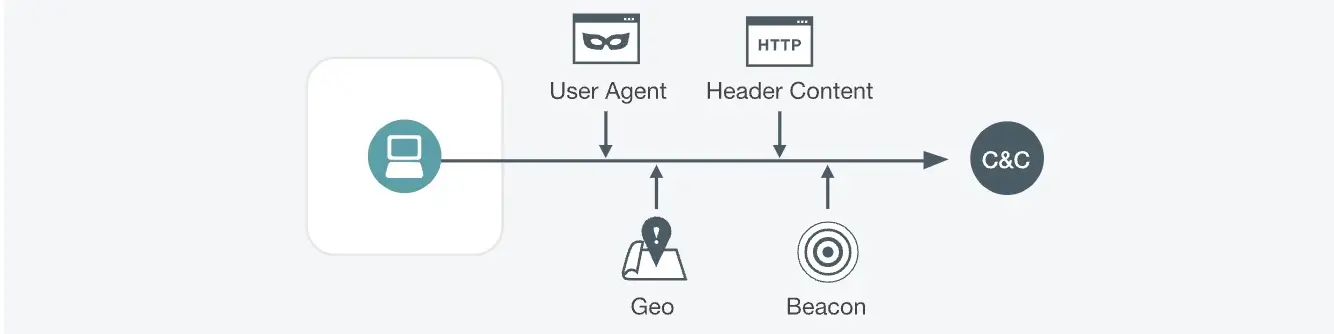
Triggers
- Software on an internal host is initiating one or more suspicious HTTP requests which form a pattern typically observed in command and control communications in recent malware samples
- The suspicious pattern may be the result of any combination of the following: (a) incorrect or malformed User-Agent, (b) absence or presence and order of a variety of HTTP headers, (c) presence and regularity of beaconing of the request and (d) connections to geographies which have a higher likelihood of hosting command and control servers
Possible Root Causes
- Malware installed on the host may be communicating back to its command and control server(s)
- Adware or spyware installed on the host may be communicating to its command and control server(s) or may be leaking data acquired on the host
- Software installed on the host is emitting HTTP requests that share two or more patterns with recent known malware samples: (a) malformed User-Agent, (b) unusual collection of HTTP headers, (c) communicating in an automated pattern and (d) communicating to out-of-the-ordinary geographies
Business Impact
- An infected host can attack other organizations (e.g. spam, DoS, ad clicks) thus causing harm to your organization’s reputation, potentially causing your IP addresses to be black listed and impacting the performance of business-critical applications
- The host can also be instructed to spread further into your network and ultimately exfiltrate data from it
- Software which infected the host can create nuisances and affect user productivity
Steps to Verify
- Look up the domain and IP address to which the communication is being sent via reputation services to see if this is known malware; such lookups are supported directly within the UI
- Search for the domain + “virus” via a search engine; this is effective for finding references to known adware or spyware
- Download the supplied PCAP and look at the HTTP payload being sent to see if any data is being leaked in clear text or whether the identity of the program is visible
- If there is no known reason why the user of the system would communicate to the geography in question, ask the end-user for a possible reason for the communication